Security Strategy for the premises of commercial and public organisations
General
Strategic buildings whether a bank, hospital or a commercial headquarters all house resources central to the integrity of their business and it is acknowledged that an appropriate level of security should be maintained to ensure operational viability and the protection of their own personnel and the public in adverse conditions. The level of security is a matter for the organisation in the context of the perceived risk and public acceptability of security measures taken.
Selecting a New Site

The security points listed below should be carefully considered when selecting a site. However, before a site or sites are selected, it is strongly recommended a security consultant is brought on to the project team to advise on the security matters associated with the proposed sites. He or she can then carry out a running security threat assessment as the principal architectural details take shape.
The Security Threat Assessment
THE SECURITY PLAN AND POLICY DOCUMENT The security policy commences with an analysis of the current threat to all qualifying assets. (An asset being a person, a material object, a procedure or process or a piece of information.) A qualifying asset is an asset considered worthy of consideration for incorporation into the security plan. The locations of all organisation's operations are relevant to the threat assessment because the structure and distribution of key assets will play an important part in the planning consideration of potential criminal or terrorist organisations. The public relations profile of the organisation and its prominence in the public eye is significant and can denote its possible popularity as a potential target by activists and criminals.
The initial analysis on the chosen locality should include:
- An analysis of the current social and environmental situation in the proposed area of the country as it may directly affect the organisation in the execution of its business.
- A review of recent security and criminal incidents within the area.
- An investigation into the access routes to the site and the industrial premises en-route and in neighbouring premises. Nearby facilities may attract crime or terrorism in their own right which could influence the operations of the organisation.
- Suitability of site and landscape to provide natural security.
The initial analysis is followed by the identification of assets and an assessment that provides a graded level of threat for each qualifying asset for all applicable risks. Threats that could be considered include:
- Armed terrorist attack and action by criminals and activists including vehicle or pedestrian borne explosive devices
- Theft of cash, armed robbery in transit, and burglary

- Theft by staff or contractors
- Theft by non staff or contractors
- Threats to personal security
- Sabotage
- Extortion, sabotage and coercion
- Fire including Arson
- Theft of information and electronic eavesdropping
- Threats to security of computer information
- Kidnap of staff or their families
- Unavailability of key staff
- Unavailability of essential items
- Essential environment failure
- Information destruction or corruption
- Communications failure
- Unauthorised intruders
- Commercial espionage
- Accidents
- Medical emergencies
- Suicide
- Riot
- Power or critical equipment failure
- Electromagnetic interference
- Natural disaster - Flood, Lightning, Earthquake
- Vandalism
The results from the analysis and assessment can be used to plan the security mitigation for the most severe risks.
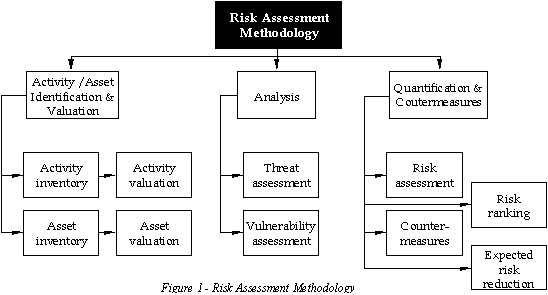
Note. For many commercial organisations a fully quantified indepth risk assessment using the above methodology is not always necessary. Often a desktop excercise is sufficient.
Security Strategy and Concept
The security strategy for any particular site will invariably be based on a combined package of security equipment, physical protection measures, a security guard force, security training and security procedures. It is likely to involve some of the items listed below:
- Physical security measures at each location combined with intruder detection equipment, CCTV, a means of controlling access and security fences.
- Building security systems. Where more than one type of system is installed, the systems should be integrated in such a manner as to ensure correct operation by the security officials and guards under all circumstances. Management systems are often desirable to audit system and operator performance and for the production of factual reports. Most of all, an effective and well managed security management system will provide accountability.
- Information, communications and computer security equipment and measures to safeguard vital information.
- A fully trained and professionally managed guard force.
- Security awareness training for an organisation's staff to improve their personal level of security in the workplace, at home and while travelling to and from the work place.
- The preparation of crisis management plans and business continuity procedures to enable management to react effectively and decisively in the event of any crisis.
It is important that the manned guard force is fully trained to effectively carry out their duties under stressful conditions. This must include the operation of the security equipment installed at each site. To facilitate this the manned guard force should be managed by an experienced security management team who will provide continuous training updates and audit reviews of procedures.
.jpg)
The Security Plan
From the security strategy a security plan or scoping document can be drawn up. The plan needs to include a survey of all project related buildings and property as it is important to try and keep uniformity of equipment and systems across the organisation where possible. For example; control, auditing and management of staff, contractors and visitors is much simpler if there is one central database that relates to all access control in the head office and other strategic areas. It can also lead to much more flexibility with regards to training and availability of in-house or contract security staff. Large savings can also be made where there is already existing or proposed maintenance staff or maintenance contractors. By increasing the duties of the maintenance staff to include first line maintenance, which does not normally require specialist expertise, expensive Supplier contracts can be greatly reduced.
The security plan is primarily aimed at high level project approval for funding and resourses, and should include:
- The standards that the implementations are to meet
- the result of the risk assessment
- summary of proposed security strategy
- means of risk management mitigation
- high level description of measures proposed per building and/or site
- project frame describing the business case, the in-house project team structure and the pros and cons for proceeding and not proceeding (SWAT analysis)
- initial project provisions required and subsequent ongoing provisions
- budget figures - typically five year TCO
- drawings.
The Security Budget
The project budget should be detailed in the security plan or scoping document (with options if necessary). It should include purchases, consultants costs, third party services, on-going maintenance and in-house costs for managing the implementation and on-going resources needed to ensure effective operations to meet the project's objectives.
Implementation of Security Plan
Once high level authorisation is given, specifications, drawings, contract documentation and tender documentation are produced and the Client's Engineer for the installation appointed. Suitable suppliers are invited to tender. Tender appraisal, preferrably based on costs, capability and experience over several years, is carried out followed by the award of contract. Installation then proceeds to acceptance testing and handover, after which a suitable maintenance contracts can be put in place.
|




.jpg)